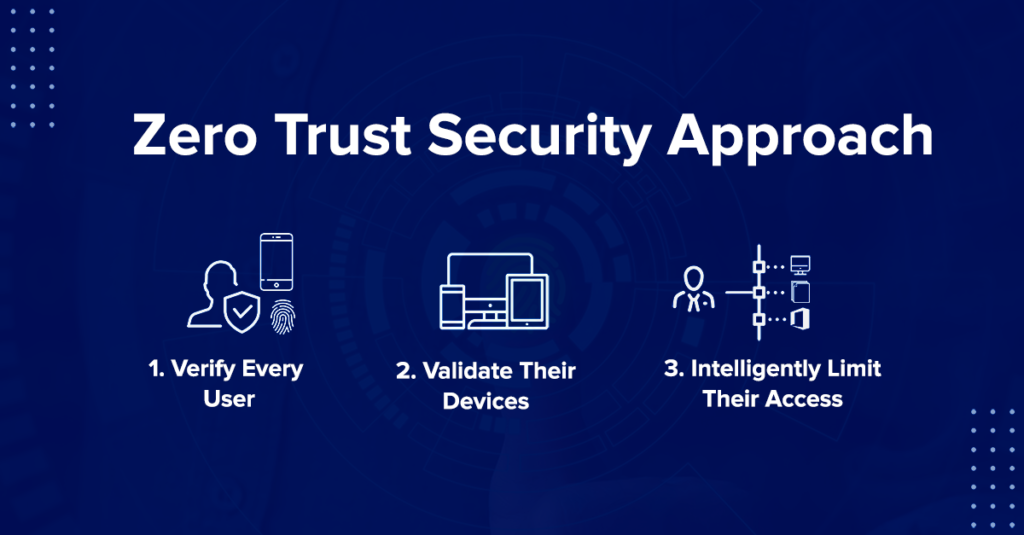
As businesses shift towards more digital, remote, and cloud-driven operations, securing networks and sensitive data has become a pressing priority. Traditional security methods that rely on perimeter-based defense are no longer enough. That’s where the Zero-Trust Security Model steps in. This article breaks down the concept in plain language and explains why modern organizations—especially in regions like Philadelphia and surrounding counties—should consider adopting it.
What is a Zero-Trust Security Model?
At its core, a Zero-Trust Security Model operates on a simple principle: trust no one, verify everyone. It doesn’t automatically trust users or devices, even if they’re inside the corporate network. Every access request is treated as if it comes from a potentially unsafe source and must be verified before any access is granted.
In other words, it means shifting from the outdated idea of a “trusted internal network” to a more dynamic and secure approach.
Why Traditional Security Models Fall Short
Legacy systems were designed for a time when most work happened on-site, and everything inside the corporate firewall was considered safe. But the rise of cloud computing, remote work, mobile devices, and cyberattacks has made this model ineffective.
Today’s threats are more complex and can come from both external and internal sources. A single compromised device can open the door to a full-blown breach. That’s why businesses—especially across Pennsylvania counties like Bucks, Montgomery, and Chester—are rethinking their cybersecurity strategies. Check out our commercial security system setup.
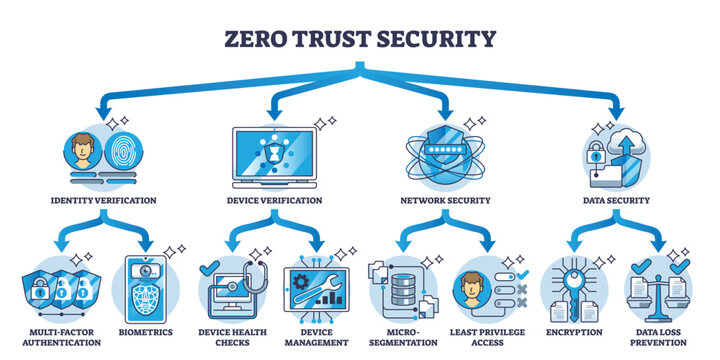
Key Elements of the Zero-Trust Approach
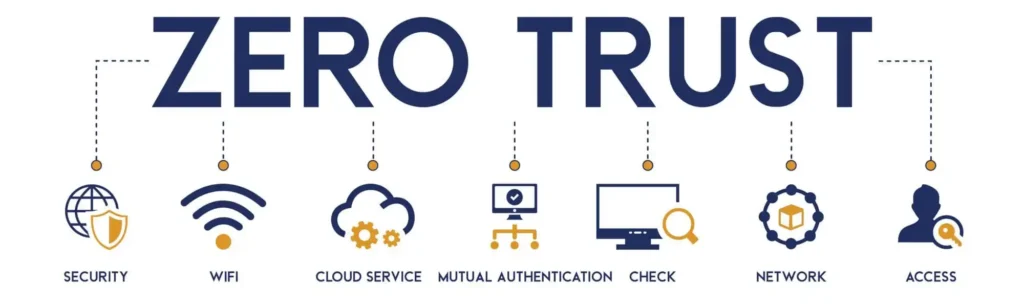
To truly understand Zero-Trust, it’s helpful to break down its core components:
1. Continuous Validation
Users and devices are constantly verified based on identity, behavior, location, and device security status—not just at login, but throughout their session.
2. Least Privilege Access
Each user only receives access to the data and tools necessary for their role. This limits the damage that can occur if an account is breached.
3. Network Segmentation
Zero-Trust breaks the network into smaller, secure sections. If a threat gets into one segment, it can’t easily spread across the system.
4. Robust Identity and Device Verification
Access requires more than a username and password. Techniques like multi-factor authentication (MFA), device health checks, and biometric verification help ensure legitimacy.
5. Assumed Breach Mentality
Rather than hoping your network is secure, Zero-Trust assumes breaches are inevitable. This mindset encourages early detection and quick response.
Why Zero-Trust Makes Sense for Modern Enterprises
1. Stronger Cyber Threat Protection
With strict access controls and constant validation, it’s much harder for attackers to navigate your network unnoticed.
2. Improved Insight and Monitoring
Security teams gain deeper visibility into who is accessing what resources and when, making it easier to spot and stop suspicious activity.
3. Regulatory Compliance Support
For businesses in regulated sectors like healthcare or finance, Zero-Trust helps meet requirements for data access, protection, and auditing.
4. Secure Remote Access
Zero-Trust enables secure remote work, ensuring that employees working from home or on the go only access approved applications and data.
5. Reduces Network Risk
Limiting who can access what minimizes the potential damage from insider threats or compromised credentials.
How to Start Implementing Zero-Trust
Rolling out a Zero-Trust model takes time, but these steps can help simplify the process:
Step 1: Identify What Needs Protection
Start by locating critical systems, sensitive data, and essential workflows that require the highest level of protection.
Step 2: Understand Who Needs Access
Audit your users and determine the minimum access they need to do their jobs effectively.
Step 3: Introduce Strong Authentication Methods
Implement MFA and enforce identity verification policies across all access points.
Step 4: Segment Your Network
Create secure zones within your network so that users and systems can only interact with what they are authorized to access.
Step 5: Set Up Continuous Monitoring
Use monitoring tools to track access patterns, flag anomalies, and respond quickly to potential threats.
Learn more about Commercial Access Control System
Tools and Technologies That Enable Zero-Trust
To make Zero-Trust a reality, organizations typically adopt tools like:
- Identity and Access Management (IAM) platforms
- Multi-Factor Authentication (MFA) solutions
- Endpoint Detection and Response (EDR) tools
- Security Information and Event Management (SIEM) systems
- Zero-Trust Network Access (ZTNA) services
- Cloud Access Security Brokers (CASBs)
These tools work together to create a layered, adaptive security environment.
Real-Life Applications of Zero-Trust
Use Case 1: Remote Workers
A company secures remote access by requiring MFA and only allowing verified devices to connect to cloud applications.
Use Case 2: Vendor Management
Third-party vendors are granted temporary, restricted access to only the systems they need, reducing exposure.
Use Case 3: Healthcare Data Protection
A medical provider uses Zero-Trust to ensure that only authorized personnel can access electronic health records, improving HIPAA compliance.
Challenges to Be Aware Of
Implementing a Zero-Trust strategy can bring a few hurdles:
- Complex Deployment: Transitioning from legacy systems can be technically challenging.
- Initial Costs: New tools and configurations may require upfront investment.
- User Resistance: Employees may be hesitant to adapt to stricter access policies.
However, the long-term security benefits far outweigh these initial challenges.
Why Zero-Trust Matters in Pennsylvania’s Business Hubs
Companies in Philadelphia, Bucks County, Montgomery County, Chester County, Delaware County, and Lehigh County face a diverse range of cybersecurity threats. From healthcare providers in Montgomery County to logistics firms in Chester County, protecting digital infrastructure is mission-critical.
Zero-Trust models offer these local enterprises a flexible, scalable, and highly secure approach to protecting data and maintaining business continuity—without relying on outdated security assumptions.
How to Choose a Zero-Trust Partner
If you’re ready to move forward with Zero-Trust, consider these selection criteria:
- Do they have experience with Zero-Trust architecture?
- Can their solutions integrate with your existing systems?
- Do they offer support for both cloud and on-prem environments?
- Is their platform easy to scale as your business grows?
Working with the right vendor ensures a smooth rollout and ongoing support.
Conclusion
Modern threats require modern solutions. Understanding Zero-Trust Security Models is no longer optional for businesses that value data protection, operational resilience, and regulatory compliance.
Zero-Trust doesn’t just reduce risk—it builds a stronger foundation for long-term success. Whether you’re a growing enterprise in Lehigh County or a tech startup in Philadelphia, adopting a Zero-Trust approach could be one of your smartest security investments.
FAQS
1. What is a Zero-Trust Security Model?
Zero-Trust is a cybersecurity framework that assumes no user or system should be trusted automatically—every access request must be verified before being granted.
2. Why is Zero-Trust important for modern businesses?
With increasing cyber threats and remote work, Zero-Trust reduces risk by constantly validating access and limiting exposure within the network.
3. How does Zero-Trust differ from traditional security?
Traditional security focuses on defending the perimeter, while Zero-Trust treats every request as potentially hostile, verifying identity and context before allowing access.
4. Is Zero-Trust only for large enterprises?
No, businesses of all sizes can benefit. Zero-Trust is scalable and can protect small and medium businesses from data breaches and unauthorized access.
5. What are the key components of a Zero-Trust model?
Core elements include multi-factor authentication, least-privilege access, continuous monitoring, identity and device verification, and micro-segmentation.
6. How does Zero-Trust support remote work?
It secures access by ensuring only trusted users and devices can access company resources, regardless of location, without relying on traditional VPNs.
7. What role does MFA play in Zero-Trust?
Multi-Factor Authentication (MFA) is a crucial layer in Zero-Trust. It adds an extra verification step to ensure the authenticity of users accessing sensitive systems.
8. Can Zero-Trust prevent ransomware attacks?
While no system is foolproof, Zero-Trust significantly reduces the attack surface, making it much harder for ransomware to spread through networks.
9. How long does it take to implement Zero-Trust?
Implementation varies by organization size and complexity. It often starts with phased rollouts focused on critical assets and high-risk users.
10. What technologies support Zero-Trust architecture?
Key technologies include identity and access management (IAM), endpoint detection and response (EDR), cloud access security brokers (CASB), and zero-trust network access (ZTNA) tools.